Arsenal & Antidote: Mapping the Tooling Landscape from Dark Web OSINT to VisibleOps Defenses
Table of Contents
The internet is a great equalizer. It hands both the miscreant and the guardian a toolbox — sometimes the same one — and asks them to do very different things with it. For defenders, this reality is the core problem and the guiding insight of effective cybersecurity: the very availability of tools lowers the barrier to entry for attackers, while defenders must assemble a far more complex, process-driven, and continuously monitored defensive stack to stay ahead.
This piece maps that asymmetry. It draws directly from a practical catalog of dark web and OSINT tools used by attackers and investigators (the ‘Dark Web Tools for OSINT Professionals’ summary) and pairs those with the defensive architecture and recommendations in the Visible OPS Cybersecurity handbook.
The Attacker’s Toolkit: Many Small Levers that Make Big Damage
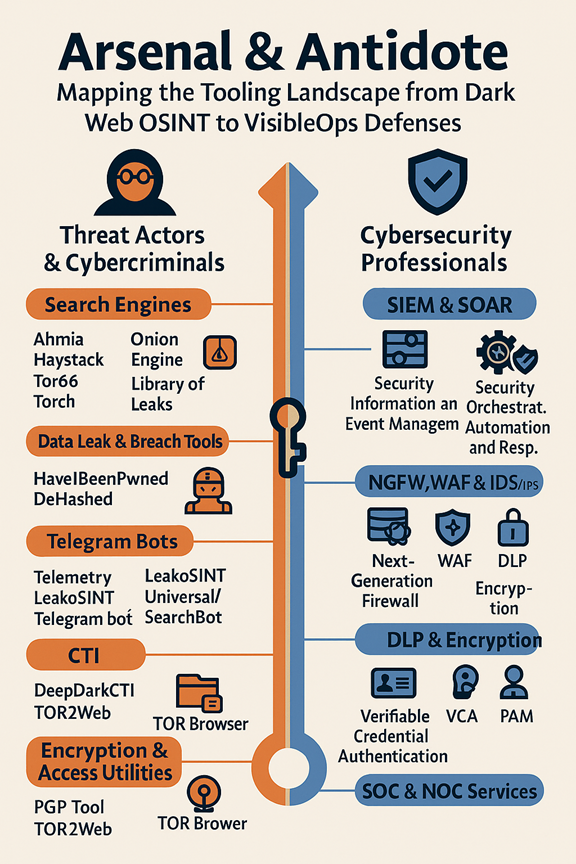
A primary lesson from the OSINT tool list is how specialized and modular an attacker’s toolkit has become. From TOR browsers to Telegram bots, attackers have a vast arsenal at their fingertips. Tools like Ahmia, Torch, and Onion Engine act as search engines for hidden .onion services, while DeHashed and HaveIBeenPwned provide data breach reconnaissance. This composable nature of dark web tools allows bad actors to chain multiple utilities into attack campaigns at scale.
The Defender’s Counter-Architecture: Processes, Telemetry, and Resilience
VisibleOps Cybersecurity emphasizes that effective defense is less about one tool and more about disciplined processes across people, processes, and technology. Core pillars like SIEM, SOAR, EDR, NGFW, and PAM only deliver true value when integrated under a governance model that enforces configuration control, change management, and Zero Trust.
Translating Attacker Capability to Defender Actions
The easiest way to make this real is to pair attacker tools with defensive responses. Leak databases map to credential hygiene; Tor-based directories link to threat intel ingestion; Telegram bots inspire automated SOAR responses; and automated crawlers highlight the need for attack surface management.
People and Process: The Secret Weapon
Most breaches succeed not through technical sophistication but human failure. VisibleOps teaches that disciplined change management, baselines, and documentation transform tools into reliable defenses. Without these, even the most advanced SOC can be overwhelmed.
A Pragmatic Roadmap for Leaders
- Inventory & baseline everything.
- Prioritize identity and credential hygiene.
- Deploy telemetry then tune it.
- Adopt threat-informed defenses.
- 5. Enforce change discipline.
Conclusion — The Asymmetric Contest Becomes Less Asymmetric When Process Wins
Attackers buy, script, and chain together tools to create a fast, adaptive offensive machine. Defenders must orchestrate people, process, and technology into a resilient posture. VisibleOps provides the blueprint: deep telemetry, governance, Zero Trust, and disciplined change control turn chaos into confidence.
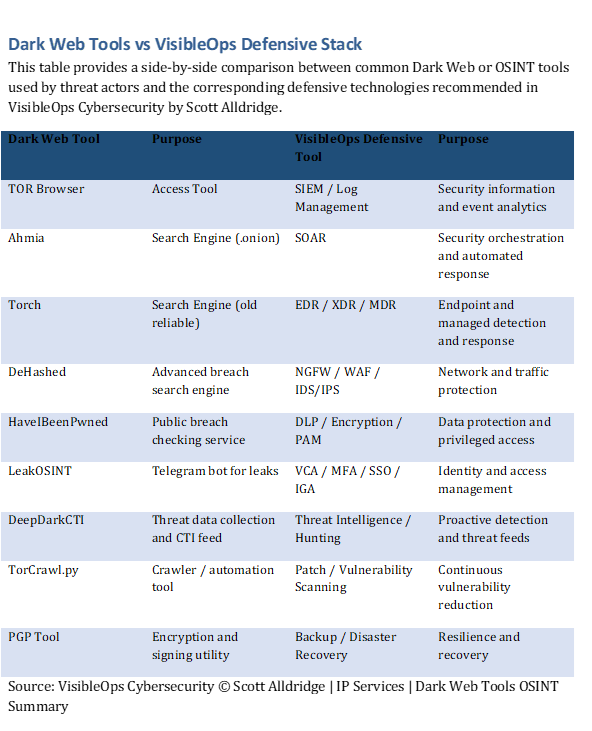
Dark Web vs Defensive Stack
This infographic below visually compares attacker toolsets and their corresponding defensive countermeasures, illustrating how VisibleOps processes align technical tools with strategic outcomes.